Linux is an open-source operating system that is based on the Unix operating system. Linux is known for its stability, security, and flexibility, and can be customized to suit the needs of the user. It is used in a wide range of applications, from servers and desktop computers to smartphones, embedded systems, and more. One of the key features of Linux is its open-source nature, which means that its source code is freely available for anyone to modify and distribute, subject to the terms of various open-source licenses.
Contents
Why Linux?
- OpenSource.
- Community support.
- Heavily customizable.
- Most Servers runs on Linux.
- DevOps most of the tools implements on Linux only.
- Automation
- Secure.
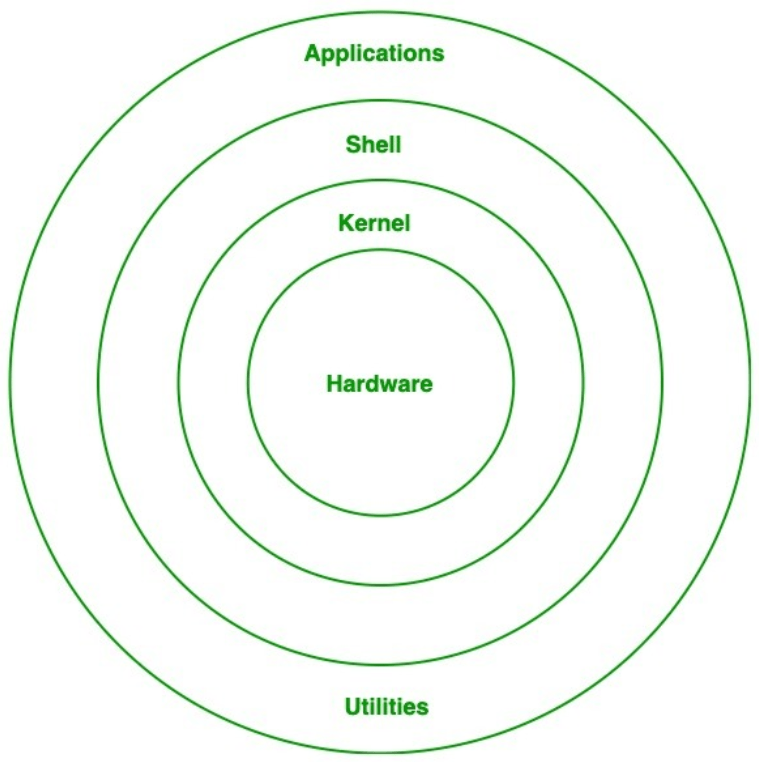
Linux Architecture
Linux Important Directories
- /bin: Contains essential executable binaries and commands that are required for basic system functionality and maintenance.
- /boot: Houses files necessary for booting the system, including the kernel, bootloader configuration, and initial RAM disk.
- /dev: Provides device files that represent hardware devices and peripherals on the system, allowing user programs to interact with them.
- /etc: Holds system-wide configuration files and directories that control the behavior of various applications, services, and the operating system itself.
- /home: Contains individual user home directories where users store their personal files, settings, and configurations.
- /lib: Contains shared libraries that are essential for system binaries and commands to function correctly.
- /media: Serves as a default mount point for removable media devices like USB drives, CD/DVD-ROMs, and external hard drives.
- /mnt: Offers a location to temporarily mount additional filesystems, such as network shares or other partitions.
- /opt: Provides a directory for optional software packages and applications that are not part of the core system.
- /proc: Presents a virtual filesystem that exposes information about running processes, kernel configuration, and system status as files and directories.
- /root: Represents the home directory of the root user, the superuser who has administrative privileges.
- /run: Stores temporary files and information needed by processes running since the last system boot.
- /sbin: Contains system binaries and commands primarily used for system administration tasks.
- /srv: Holds data and files for services provided by the system, often used by web servers and other network services.
- /sys: Offers a virtual filesystem that exposes information about devices, drivers, and kernel settings.
- /tmp: Stores temporary files and directories created by applications and processes. Contents are typically cleared upon system reboot.
- /usr: Contains user-related programs, libraries, documentation, and resources for both system administrators and regular users.
- /var: Houses variable data files, including log files, caches, spool directories, and other dynamic data generated by applications and services.
50 important Linux commands:
1. cd
cd <directory path>cd stands for “change directory”. It is used to change the current working directory.
2. ls
lsls stands for “list”. It is used to list the contents of a directory.
ls -aThe -a option is used to show all files and directories, including hidden files
ls -lThe -l option is used to display the results in a long format
ls -RThe -R option is used to display the results recursively, i.e., it will show the contents of all subdirectories as well.
3. pwd
pwdpwd stands for “present working directory”. When you run the ‘pwd’ command, it will display the full path of the current directory in the terminal
4. mkdir
mkdir <folder name>mkdir stands for “make directory”. When you run the ‘mkdir’ command, it will create a new directory with the name you specify.
mkdir -p example/example2This command will create the “example” directory if it doesn’t already exist, and then create the “example2” directory inside it
5. rm
rm <file name>
rm -r <folder name>rm stands for “remove”. It is a command used in the Linux terminal to remove files.
6. mv
mv <source> <destination>mv stands for “move”. When you run the ‘mv’ command, it will move the specified file or directory to a new location, or rename the file or directory.
7. cp
cp <source> <destination>cp stands for “copy”. When you run the ‘cp’ command, it will create a copy of the specified file or directory in a new location
To copy all data which starts from D alphabet
cp -rvf /root/D* /home- -r for recursive
- -v for verbose
- -f for forcefully
8. touch
touch <file name>touch command is used to create a new empty file or update the timestamp of an existing file.
stat hello.txt
touch -a hello.txt // to change access time
touch -m hello.txt // to change modified time
touch hello.txt // to change alltouch .file.txtThis command is used to create hidden file
touch test-{1..4}.txt9. sudo
sudo <command you want to run>sudo is a command that allows a user with administrative privileges (i.e., the “superuser”) to execute a command with elevated permissions.
Note: It’s important to note that you should only use ‘sudo’ when necessary, as it can be dangerous to run commands with elevated permissions if you’re not sure what the command will do
sudo su satyam The command “sudo su satyam” is used to switch to the user satyam
sudo su The command “sudo su” is used to switch to the root user
To exit type exit
10. rmdir
rmdir <folder name>rmdir is used to remove an empty directory. If the directory contains files or other directories, the ‘rmdir’ command will fail
rm -rfremoves non-empty file and directory
11. cat
cat <file name>cat command is used to display the contents of a file on the terminal.
cat > hello.txtcat > file2.txt creates a new file named file2.txt and allows you to enter text into that file from the terminal
cat >> hello.txtcat hello1.txt >> hello2.txtThis command is used to append the contents of one file to another file.
cat hello1.txt > hello2.txtWhen this command is executed, the contents of hello1.txt are written to hello2.txt. If hello2.txt already exists, its contents are overwritten with the contents of hello1.txt. If hello2.txt does not exist, it is created and the contents of hello1.txt are written to it.
cat hello1.txt hello2.txt > hello3.txtThis command is used to concatenate the contents of two files and redirect the output to a third file
12. echo
echo "Hello, World"echo command is used to display a string of text on the terminal.
13. clear
clearclear command is used to clear the terminal screen. It will remove all the previous commands, outputs, and prompts from the terminal window, making it appear as if you have a fresh terminal window open.
14. history
historyhistory command is used to display a list of previously executed commands in the terminal.
15. wc
It is used to count the number of lines, words, and characters in a given text file
wc -l /etc/passwd
wc -w /etc/passwd
wc -c /etc/passwd16. ping
ping hostnameping command is used to test the connectivity between two networked devices, such as a local machine and a remote server. The ping command sends a small packet of data to the remote device and waits for a response. If a response is received, it indicates that the two devices are connected and able to communicate with each other
17. whoami
whoamiwhoami command is used to display the username of the current user. When you log in to a Linux system, you are assigned a unique username that identifies you to the system.
18. hostname
hostnamehostname command is used to display the hostname of the current system. The hostname is the name given to a computer or device on a network
19. zip/unzip
zip <archive name> <file names separated by space>
unzip <archive name>zip command is used to compress files and create zip archives, while the “unzip” command is used to extract files from zip archives
20. man
man [command_name]man command is used to display the manual page for a particular command or topic
Press q to quit
21. alias
alias newcommand='originalcommand'alias command is used to create a shortcut or alternate name for a command or group of commands.
22. diff
diff file1 file2diff command is used to compare the contents of two files and highlight the differences between them. The diff command is often used in software development and system administration to compare different versions of files, or to identify changes made to a file over time.
23. head/tail
head -3 filename
tail -3 filenamehead command displays the first few lines of a file.
tail command displays the last few lines of a file
24. cmp
cmp file1 file2cmp command is used to compare two files byte by byte and display the differences between them. The cmp command is often used in software development and system administration to check for changes made to a file, or to verify that two files are identical.
25. passwd
passwdpasswd command is used to change a user’s password.
26. wget
wget [URL]wget command is used to download files from the internet. By default, the file will be saved with the same name as it has on the web.
27. which
which gitIt allows you to locate the location of a specified executable file in the system’s path.
28. tr
tr set1 set2tr command is used to translate or delete characters. It takes two sets of characters and replaces any occurrences of characters in the first set with the corresponding characters in the second set. If the second set is shorter than the first, any extra characters in the first set will be deleted.
29.
sudo apt update
sudo apt upgrade
sudo apt install tree
sudo apt purge treesudo apt updateupdates the local package lists. It does not install or upgrade any packages; it only refreshes the local package index.sudo apt upgradeactually upgrades the installed packages on your system to their latest versions.sudo apt installcommand is used to install software packages.- The
sudo apt purgecommand is used to completely remove a package and its associated configuration files from the system.
30. find
find [expression]find command is used to search for files and directories in a specified location. It is a powerful command that allows you to search for files based on various criteria such as name, size, type, modification date, and ownership
find *.txtfind /downloads -name key.pemTo search a file with less than 10MB in a folder
find /downloads -size -10MTo search a file with more than 10MB in a folder
find /downloads -size +10MUsing find command based on users
find / -user rootUsing find command based on groups
find / -group groupname31. locate
locate [expression]locate command is used to search for files and directories in a database of the file system. This command is much faster than the find command because it searches a pre-built database instead of searching the entire file system
32. chmod
chmod mode <file_name>chmod command is used to change the permissions of files and directories. It stands for “change mode” and is used to specify who can read, write, or execute a file
The mode argument specifies the new permissions to be set, and can be represented in two different formats:
- Numeric: The permissions are represented by a three-digit number, with each digit corresponding to a different category of user (owner, group, and others). The digits represent the sum of values assigned to each of the permissions (read=4, write=2, execute=1). For example,
chmod 644 myfile.txtsets read/write permissions for the owner and read-only permissions for everyone else. - Absolute: For example,
chmod u+r myfile.txt(add read permission to owner),chmod g+rw myfile.txt(add read/write permission to group),chmod o-r myfile.txt(remove read permissions to others)
To view file permissions
ls -l file_nameExample:
-rw-r--r-- 1 user group 1024 Jul 10 10:30 example.txt
-rw-r--r--: This part represents the file permissions1: This number indicates the number of hard links to the file.user: This is the username of the file’s owner.group: This is the group name to which the file belongs.1024: This number indicates the file size in bytes.Jul 10 10:30: This is the date and time when the file was last modified.example.txt: This is the name of the file.
To view directory permissions
ls -ld <directory_path>
33. chown
chown new_owner <file_name>chown command is used to change the ownership of a file or directory. It stands for “change owner” and is often used to transfer ownership from one user to another
For changing group owner
chown group_name <file_name>34. chgrp
To change group of a file
sudo chgrp devops demofile.txt35. grep
grep pattern [file(s)_name]grep command is used to search for specific text patterns within one or more files. The name grep stands for “global regular expression print”
Some common options for the grep command include:
-i: Ignores case when searching-v: Inverts the search, i.e., returns all lines that do not match the pattern-r: Recursively searches through directories
To search a word
grep root /etc/passwdTo search a word in multiple files
grep root /etc/passwd /etc/groupTo search a string insensitive in file
grep -i Root /etc/passwdTo search a string in all files
grep -r root /To inverts the search, i.e., returns all lines that do not match the pattern
grep -v root /etc/passwdTo display the file names that match the string
grep -l root /etc/passwd /etc/groupTo display the file names that do not match the string
grep -L root /etc/passwd /etc/groupTo display the string match total line number
grep -c root /etc/passwdTo display the string match line with number
grep -n root /etc/passwdTo display the lines that start with a string
grep ^root /etc/passwdTo display the lines that end with a string
grep root$ /etc/passwdTo search and redirect output into a new file
grep root /etc/passwd > demo.txt36. top
toptop command is used to monitor the system’s processes and their resource utilization. It provides a real-time, dynamic view of the processes running on a system, showing which processes are using the most CPU time, memory, and other system resources
- PID: The process ID number
- USER: The user that owns the process
- PR: The priority of the process
- NI: The nice value of the process
- VIRT: The virtual memory used by the process
- RES: The resident memory used by the process
- SHR: The shared memory used by the process
- S: The state of the process (running, sleeping, etc.)
- %CPU: The percentage of CPU time used by the process
- %MEM: The percentage of memory used by the process
- TIME+: The total CPU time used by the process
37. kill
kill PID(s)kill command is used to terminate a process by sending it a signal. A signal is a software interrupt that can be used to communicate with a running process
38. uname
uname
uname -runame shows the name of the kernel (OS)
uname -r shows the version of the kernel
39. useradd
useradd usernameuseradd command is used in Linux to create a new user account
Note: When you create a new user account with useradd, you will need to set a password for the account using the passwd command before the account can be used.
passwd usernameIf we want to check all users
sudo cat /etc/passwdTo check user account properties
grep satyam /etc/passwdTo check user password properties
grep satyam /etc/shadowgroupadd command is used in Linux to create a new group
groupadd groupnamegpasswd -a satyam groupname # To add single member in a groupgpasswd -M satyam,rahul groupname # To add multiple member in a groupIf we want to check all groups
sudo cat /etc/groupTo check group account properties
grep groupname /etc/groupTo check admin properties
grep groupname /etc/gshadow40. userdel
userdel usernameuserdel command is used in Linux to delete a user account
Note: When you delete a user account with userdel, all files and directories associated with that user account will be removed. Be sure to back up any important data before deleting a user account
groupdel groupnamegroupdel command is used in Linux to delete group
gpasswd -d satyam groupname # To remove group membergpasswd -A satyam groupname # To make group admin41. lscpu
lscpulscpu command is a Linux command that is used to display information about the CPU architecture of the system. It is useful for identifying the number of processors, cores, threads, and their respective speeds, as well as other details about the CPU architecture
42. ifconfig
ifconfig is used to display network interface configuration information on Unix-like systems. It displays information about all active network interfaces on your computer, such as their IP addresses, MAC addresses, and network-related statistics
43. tree
treedisplays the directory structure in a tree-like format
44.
cat /etc/os-release
lsb_release -aIt is used to display information about the operating system installed on a Linux system. It typically shows details such as the operating system name, version, and other related information.
45. ln
ln <source_file> <target_link>: This creates a hard link between thesource_fileand thetarget_link. Both the source file and the target link will point to the same underlying file data on the disk. If you make changes to either the source file or the target link, it will reflect in both.ln -s <source_file> <target_link>: This creates a symbolic link (also known as a soft link) between thesource_fileand thetarget_link. A symbolic link is a special type of file that acts as a pointer to the source file.
46. awk
It allows you to perform various text manipulation tasks.
awk 'pattern { action }' input_fileawk 'NR>=1 && NR<=20 && /TRACE/ {print NR,$1,$2,$5}' application.log > final.log47. tar
tar stands for “tape archive” and is used to create, view, and extract files from an archive file or a collection of files compressed into a single file.
-c: Create a new archive.-x: Extract files from an existing archive.-v: Verbosely display progress and file names being processed.-z: Compress the archive using gzip.-j: Compress the archive using bzip2.-t: List the contents of an archive.-C: Change to a specific directory before performing any operations.
Create a new archive of files
tar -cvf archive.tar file1.txt file2.txt
tar -cvf /folder/archive.tar file1.txt file2.txtExtract files from an existing archive
tar -xvf archive.tar
Create a compressed archive using gzip
tar -cvzf archive.tar.gz file1.txt file2.txt directory/
Extract files from a compressed archive using gzip
tar -xvzf archive.tar.gz
Create a compressed archive using bzip2
tar -cvjf archive.tar.gz /var48. systemctl
It provides a convenient way to start, stop, enable, disable, and view the status of various services and daemons on the system
To view status
systemctl status <service_name>
systemctl status dockerTo start a service
systemctl start dockerTo stop the specified service
systemctl stop dockerTo stop and then start the specified service
systemctl restart dockerThis command configures the specified service to start automatically when the system boots up
systemctl enable <service_name>
This command prevents the specified service from starting automatically on system boot
systemctl disable <service_name>
Vim vs Nano editor
nano example.txtThis will open a new file named “example.txt” in Nano.
Start typing your text and when you are finished, press “Ctrl” + “O” to save your changes. To exit Nano, press “Ctrl” + “X”
vim example.txtThis will open a new file named “example.txt” in Vim.
Press the “i” key to enter insert mode and start typing your text. When you are finished, press the “Esc” key to exit insert mode. To save your changes, type :w and press Enter. To exit Vim, type :q and press Enter.
It has 3 modes:
- Command Mode
- Insert mode (edit mode)
- Extended command mode
Note: When you open the vim editor, it will be in the command mode by default.
base64
The base64 command is used to encode and decode data using the Base64 encoding scheme
To encode a string, use the following command:
echo "Hello, world" | base64This command encodes the string “Hello, world!” and displays the encoded output on the terminal.
To decode a string, use the following command:
echo "SGVsbG8sIHdvcmxkIQ==" | base64 --decodessh
ssh command is used to securely connect to a remote server or device over a network. The ssh command uses the SSH (Secure Shell) protocol to establish a secure connection between the local and remote machines, allowing you to perform remote operations on the remote machine as if you were sitting in front of it